








CCTV Camera & Access Control
Pairing access control and CCTV systems helps generate smarter video data for the security system. Consider, for example, an access control system that uses proximity cards. Without a CCTV system, someone who shouldn't have access to a building could get access by using a lost or stolen card. Backed by Team of Engineers, we help you to install and repair both devices at your place.
CCTV Camera Installation
When it comes to securing your business, there are many different types of CCTV to choose from. Surveillance plays a huge part in today’s society, and with cameras all around us, our day-to-day lives are experiencing higher levels of security each day.
CCTV plays a huge part in today’s society, and with cameras all around us, our day-to-day lives are experiencing higher levels of security each day. What many people don’t know, however, is that there are a variety of different types of CCTV camera which suit different situations or premises, and that selecting the proper camera for the right application really is vital.
Our CCTV Camera Services
We can accommodate for any budget, providing security solutions to all domestic, commercial, retail and industrial customers!
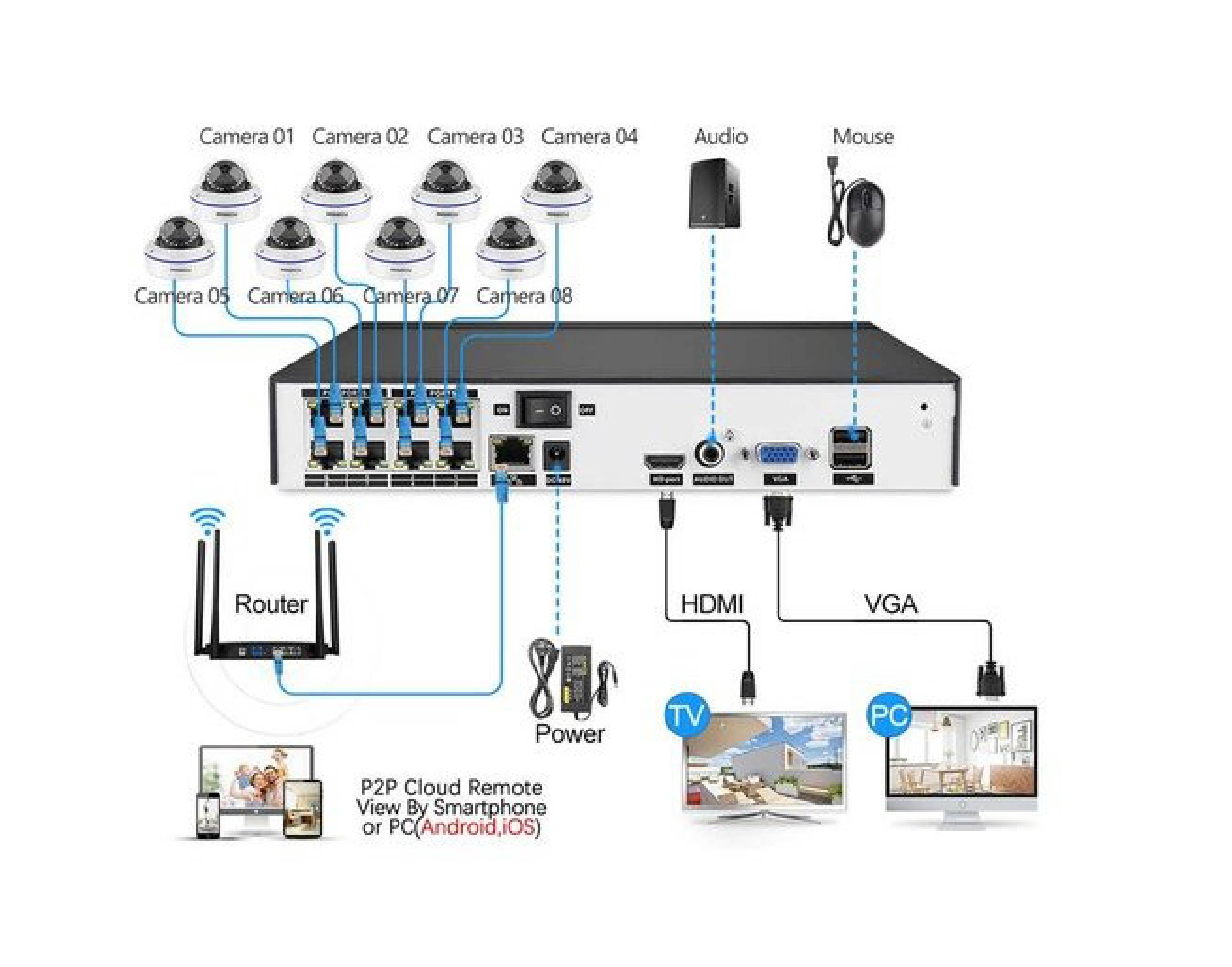
CCTV Installation

Long Distance Automation Monitoring

IP Surveillance System

Ground & Street CCTV Security System
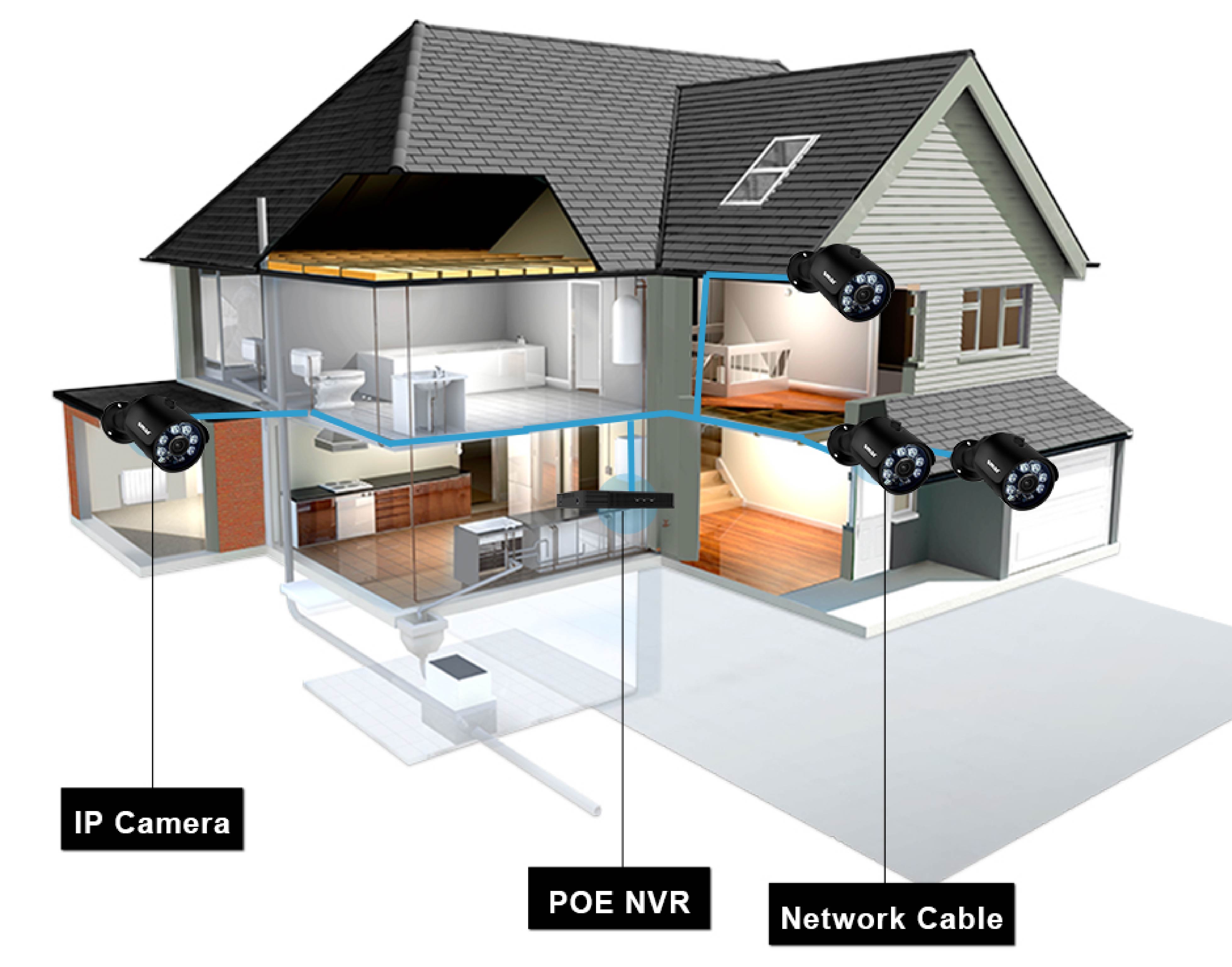
Home CTTV Camera Installation Security

We Supply Home & Office CCTV Security
Key Features
High Security
a surveillance security system typically consisted of several cameras connected—either hardwired or wireless— to a digital video recorder (DVR), which recorded the images and displayed them on a closed circuit television (CCTV) or monitor.
Full Device Protection
We help you to control your divices at market or factory wherever you are by installing wireless security cameras deliver the most features, have the best Wi-Fi connectivity. implementing highest security in your organisation is our task!
Remote Monitoring
We help you to control your home-business or factory wherever you are by installing wireless security cameras deliver the most features, have the best Wi-Fi connectivity, and offer perks like free cloud storage. wireless security cameras.
Full Backup of Information
with CCTV Camera Records, our Team of technicians install and configure NVR or DVR Camera Recorder, and every recorded information be kept till you need. we help you to keep your recorded information secured
Access Control Installation
When it comes to Access control we help you to secure your Business! as Access Control is a security technique that regulates who or what can view or use resources in a computing environment. It is a fundamental concept in security that minimizes risk to the business or organization. There are two types of access control: physical and logical.
We help you to set up Three Types of Access Control Systems. Access control systems come in three variations: Discretionary Access Control (DAC), Mandatory Access Control (MAC), and Role-Based Access Control (RBAC).
Our Biometrics Services

Access Control Installation

Fingerprint Door Set up

Access Contol Set up

Access Control Confuguration

Access Control Maintenance

Home & Office Security
Key Features
High Security
Keys have now passed the baton to computer-based electronic access control systems that provide quick, convenient access to authorized persons while denying access to unauthorized ones.
Full Device Protection
This is done by building device protection mechanisms into the physical device and ... This eliminates the intermediary VMM/IDD on the device access path and we make sure that your access device installer is safe and secured
Remote Monitoring
Remote monitoring is an efficient and cost effective security measure. Our experienced team are ready to help you find the right remote monitoring solution and package, whether you are a business premises or an installer.
Full Backup of Information
During backups, the metadata information associated with the files is collected, stored in the backup index, and is available for search or browse. By default, end-users can browse and search all the data backed up from a common resource like a shared laptop or file server. You can restrict end user access on such common resources by enabling access control on the client data.







